Mozilla's Firefox Invalid, Yet Valid Certificate
 Sunday, April 1, 2012 at 21:59
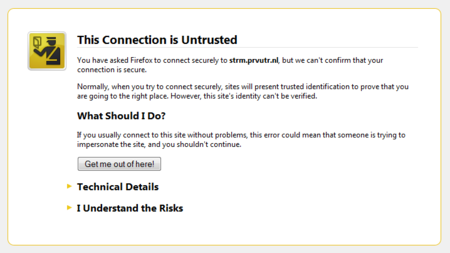
Sunday, April 1, 2012 at 21:59 In my line of work I get to work with a lot of security devices which run self-signed certificates. Those certificates are most of the time generated when the device / appliance is installed, or configured for the very first time. When you connect to one of those devices with a web browser, you tend to see the warnings displayed by the browser that the connection is not to be trusted.
In Firefox, you can add an exception in the browser. When you've done that, the next time you go to the website, the browsers treats the website as trusted.
 FireFox,
FireFox,  PKI,
PKI,  certificates in
certificates in  Annoying,
Annoying,  Browsers,
Browsers,  Tips'n Tricks
Tips'n Tricks