Cisco Secure ACS 5.x and Apple OSX Directory (LDAP)
 Tuesday, March 1, 2011 at 13:50
Tuesday, March 1, 2011 at 13:50 For testing and development purposes I run a Cisco Secure ACS 5.x in a virtual machine at home. In this environment I also run an Apple Directory Service. I'll be using this setup to test several 802.1x and RADIUS authentication schemes.
To get things going I needed to connect to the ACS to my LDAP Directory. The Apple Directory Service is a bit different from the regular LDAP implementations. They seem to add the 'apple' reference in a lot of attribute values. Thankfully the ACS has a very versatile configuration interface.
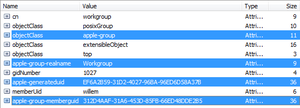 Apple references in attribute valuesNormally, the group definition would be 'group' instead of 'apple-group'. So the configuration of the ACS should reflect these variations to the standard.
Apple references in attribute valuesNormally, the group definition would be 'group' instead of 'apple-group'. So the configuration of the ACS should reflect these variations to the standard.
 Willem |
Willem |  4 Comments |
4 Comments |  ACS,
ACS,  Cisco,
Cisco,  Directory Service,
Directory Service,  LDAP in
LDAP in  Apple,
Apple,  Security,
Security,  Software,
Software,  Tips'n Tricks
Tips'n Tricks