Cisco Secure ACS 5.x and Apple OSX Directory (LDAP)
 Tuesday, March 1, 2011 at 13:50
Tuesday, March 1, 2011 at 13:50 For testing and development purposes I run a Cisco Secure ACS 5.x in a virtual machine at home. In this environment I also run an Apple Directory Service. I'll be using this setup to test several 802.1x and RADIUS authentication schemes.
To get things going I needed to connect to the ACS to my LDAP Directory. The Apple Directory Service is a bit different from the regular LDAP implementations. They seem to add the 'apple' reference in a lot of attribute values. Thankfully the ACS has a very versatile configuration interface.
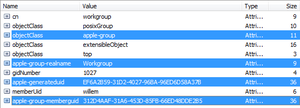 Apple references in attribute valuesNormally, the group definition would be 'group' instead of 'apple-group'. So the configuration of the ACS should reflect these variations to the standard.
Apple references in attribute valuesNormally, the group definition would be 'group' instead of 'apple-group'. So the configuration of the ACS should reflect these variations to the standard.
The following screenshots show the LDAP connector for an Apple Directory Service.
The first screenshot shows the initial configuration of the ldap connection. This is pretty straightforward. I use a secure connection, and I recommend you doing the same. This way the information exchange between the ACS and the LDAP is always encrypted. For testing purposes this is usually left out.
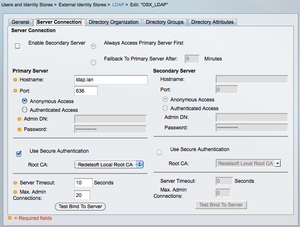 Initial Connection SettingsNext comes the 'different' part. The default values of the 'Group Objectclass' and 'Group Map Attribute' are different from what is displayed in the screenshot. The information needed for a correct Apple Directory connection are:
Initial Connection SettingsNext comes the 'different' part. The default values of the 'Group Objectclass' and 'Group Map Attribute' are different from what is displayed in the screenshot. The information needed for a correct Apple Directory connection are:
Group Objectclass: apple-group
Group Map Attribute: memberUid
The other difference is that the 'Subjects In Groups Are Stored In Member Attribute As:' should be changed to 'username' instead of 'distinguished name'.
The Subject (and Group) Search Base are, again, straightforward (basic LDAP functionality).
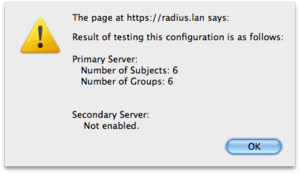
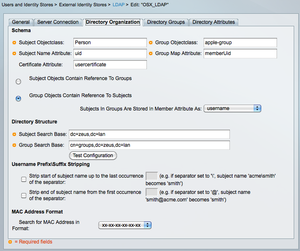 Settingof the User and Group attributes and the search DN'sHitting the 'Test configuration' button should display a pop-up showing at least some users and groups that were found in the LDAP.
Settingof the User and Group attributes and the search DN'sHitting the 'Test configuration' button should display a pop-up showing at least some users and groups that were found in the LDAP.
 Finally, you can select Directory groups that can be used in the RADIUS (or TACACS) policies on the ACS.
Finally, you can select Directory groups that can be used in the RADIUS (or TACACS) policies on the ACS.
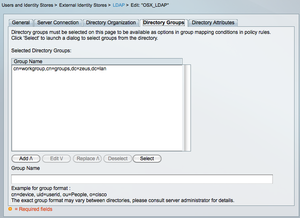 Selection of Directory Groups in your ACS policies
Selection of Directory Groups in your ACS policies
Now, everything is ready to start experimenting with RADIUS (and/or TACACS).
 Willem |
Willem |  4 Comments |
4 Comments |  ACS,
ACS,  Cisco,
Cisco,  Directory Service,
Directory Service,  LDAP in
LDAP in  Apple,
Apple,  Security,
Security,  Software,
Software,  Tips'n Tricks
Tips'n Tricks 

Reader Comments (4)
Hi all,
I read this post with great interest since I have the following problem @ a large customer site:
Customer wants to do machine-authentication against ACS 5.x --> OpenLDAP by checking only the clients MAC-address against the MAC-addresses stored in LDAP. If there is a match the client will get access to e specific SSID and subsequent VLAN.
If anyone faced the same situation in the past I would really appreciate to get some further infos about configs etc.
Many thanks in advance; best regards
RHUB
Hi Roman,
not sure what you mean by "If there is a match the client will get access to e specific SSID and subsequent VLAN". SSID selection assigment is a client (supplicant) issue. You can't force a client to a specific SSID when he/she authenticates.
Normally you would have a couple of SSID's available where one is used for corporate access. Based on the authentication the client would be assign a VLAN in the access point or wireless controller, but the SSID stays the same. Other SSID's are usually used to provide other access services (e.g. Guest Access).
Hope this helps.
If you have other questions, you can also contact me through the contact form
Hi Willem,
Many thanks for your reply. I again went through my post and of course you're right. I realized that I wrote something about SSID selection, which is definitely wrong; sorry about the missleading words.
I was at customer site yesterday and currently I'm facing the following problem:
In the 1st step of the auth.-process the customer wants to check the MACs (MAC OS-X) MAC_address either against external identity store (Open LDAP) or against the internal identity store; the clients are defined in either one of these stores by their MAC_addresses. Goal of this step is to prevent devices not belonging to the the customer from accessing the WLAN.
The 2nd step authorizes checks if the users are in LDAP and VLAN-assignment is done according to some rules.
The problem is that the user-authentication works perfectly but the machine-auth doesn't.
I'm expecting the client to present its MAC_address to ACS for checking it either against Open-LDAP or internal identitiy store (for hosts).
But instead of presenting its MAC_address, the client presents the user login infos (xyz), which is definitely not in either identity store.
I'm not a MAC-guy but according to the customer all the definitions on the MACs are correct.
According to your post, I assume that you have made extensive experiences in this area.
I really appreciate if you could give me a hint or even better send me some screenshots of a functional environment.
Many thanks in advance and best regards
Roman
I've tried exactly what you've suggested, but it doesn't work for me. I have a Open Directory configured on Mountain Lion. Any advice?